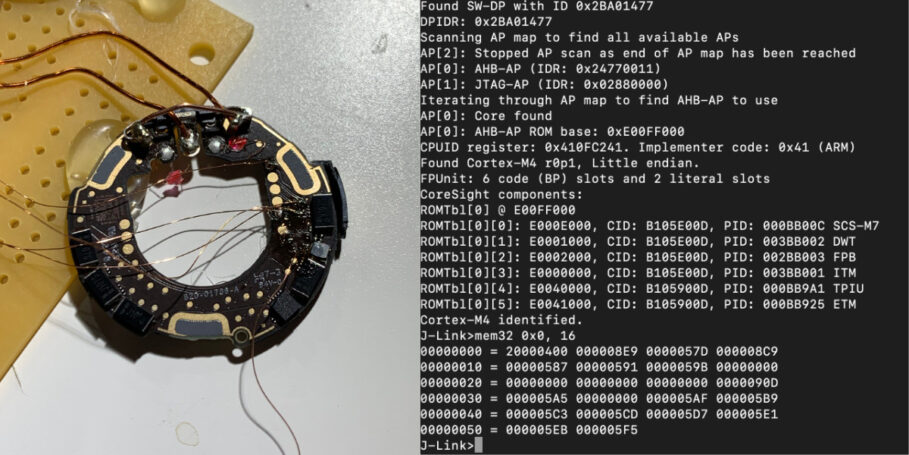
A security researcher was successful in hacking the AirTag by reverse-engineering its microcontroller. This is apparently the first time an AirTag was hacked or, say, “Jailbroken”.
German security researcher and YouTube content creator that goes by the name Stack Smashing tweeted today that they were successful in “breaking into the microcontroller of the AirTag.” They were then able to re-flash the microcontroller that enabled them to modify elements of AirTag’s software.
A microcontroller is an integrated circuit (IC) used for controlling devices usually via a microprocessing unit, memory, and other peripherals. According to AllAboutCircuits, “these devices are optimized for embedded applications that require both processing functionality and agile, responsive interaction with digital, analog, or electromechanical components.”
That said, gaining control over the microcontroller essentially means allowing the hacker to decide what they need the device to do. In this case, the security researcher Stack Smashing quickly demonstrated one of the things they could do with their “Modified AirTag.” They tweaked the URL that appears within a notification when an AirTag enabled in Lost Mode is tapped on by an NFC-enabled device (which includes smartphones other than iPhones) to promote their own website. Usually, the AirTag will redirect to a “found.apple.com” website for displaying Lost Mode information related to the owner.
This might be just the first of many demonstrations of what a hacked AirTag is capable of doing. Also for what seems to technically be the first “Jailbreak” for AirTag, it’s unclear as of now to what extent a hacker can tinker with the device.
Regardless, chances are Apple won’t be happy hearing about it. Hacking an AirTag ought to come along with security implications. Since it’s a tracker used to track things, a modified version of it could be used by miscreants for their own malicious intents. It’s unclear as of yet what security measures Apple has in place to avoid this from happening.
However, the security researcher did claim that while trying to reverse engineer the microcontroller, he bricked two of his AirTags.
At the moment, it’s also unclear if Apple would implement some sort of server-side blocking mechanism to block a modified AirTag from accessing its Find My network. But that’s a likely possibility.
Let us know your thoughts in the comments section below.
Note: This story contains affiliate links that may earn The 8-Bit commissions on successful purchases to help keep the site running.